40 with contemporary antivirus protection it is now possible
The best antivirus software 2022 - TechRadar The best antivirus for 2022. You may be more familiar with names such as Norton, McAfee and AVG - but Bitdefender has been the overall best antivirus available for a few years now. It combines ... COSC 1301 quiz ch.1 Flashcards | Quizlet With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer false looking for a keyboard to project from a device to a flat surface, which would you use virtual keyboard user that requires capabilities of a powerful computer power
Coronavirus: How COVID-19 is changing the world - Monash Lens The sweeping impact of the novel coronavirus and the disease it causes, COVID-19, is unprecedented in our lifetimes. Leading academics Monash University's Faculty of Arts offer their views on what's unfolding, the implications, and how it could reshape relationships, governments, and broader society. Read more at Monash Lens.
With contemporary antivirus protection it is now possible
Car Computer Virus? Modern Hackers Could Control Your Car According to Aryeh Goretsky, a researcher at a technology security company called ESET, you shouldn't be too worried. Goretsky states that creating a virus for a car computer is expensive because vehicle manufacturers have proprietary hardware and software. So, attackers could only target one specific make and model at a time. Antivirus evasion techniques show ease in avoiding ... This test simply demonstrates that it is possible to bypass antivirus engines using this methodology. There are still plenty of other methods that can be utilized to bypass all of them. Packaging Exploits With Penetration-Testing Frameworks My next test utilized the popular Metasploit Community Edition penetration-testing framework. What is the future of UK leadership in global health ... The UK is a global health leader. Since the concept of 'health security' first came into parlance with the reconceptualisation of HIV/AIDS as a security threat, 1 the UK has been a leader on global health security. This position was solidified by the broader movement towards the securitisation of non‐traditional security threats post 9/11 (and indeed the anthrax attacks). 2
With contemporary antivirus protection it is now possible. (PDF) Computer Security and Mobile Security Challenges Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well... How to Test Antivirus (Is it Really Working and Protecting ... If you have active protection working properly, the simple act of saving the file should trigger an alert. In case the EICAR file is not detected, something is either wrong with your antivirus program, or you are using a rogue or fake security solution. Almost all antivirus applications are able to detect this file and mark it as a threat. Contemporary survey on effectiveness of machine and deep ... The importance of the cyber security is on the rise because social media pages now publish personal information which could lead to identity theft. Since most of the sensitive data like credit/debit card and bank account numbers are stored using cloud such as Dropbox and Google Drive, data security is vital everywhere [5] . conveys meaning and is useful to one or more people 2pts ... 7) ____ conveys meaning and is useful to one or more people. (2pts) Data Information Hardware Software 8)With contemporary antivirus protection, it is now possible to ensure a virus or malware never will attack your computer. (2pts) True False False
ESET named a Major Player in two Modern Endpoint Security ... From endpoint and mobile security to endpoint detection and response, as well as encryption and multi-factor authentication, ESET's high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defences in real time to keep users safe and businesses running without interruption. PDF MODERN PROTECTION AGAINST ATTACkS FROM THE INTERNET gurations should be possible in a centralized manner via the system. Higher security standards were called for in the e-mail system in Kiel too. The aim: to ensure greater protection against spam and malware such as viruses and Trojans. THE SOLUTION Thanks to a next generation firewall, the security system at the FH Kiel is now up to date. Role of technology in COVID-19 pandemic - PMC It is a blend of medical devices and software applications connected to healthcare IT systems. In the current critical scenario of nCOVID-19, the most significant issue after the development of vaccine is an efficient way of reachability to the patients. This can be best done by using the concept of IoT. PDF SIMATIC PCS 7 V9 - Siemens Protection at management and operational level With the end of support for operating systems, plant owners/ operators face an increased security risk due to the lack of security-relevant updates. The consequence: Newly discov-ered vulnerabilities are no longer closed and can thus be exploited unhindered by cybercriminals. Version 9.1
What is Antivirus Software? Download Free Antivirus ... - ESET A reliable security solution with multiple layers of advanced technologies can detect, neutralize and remove even deeply embedded malware, protect users from ransomware, spyware, spam, phishing and other social engineering techniques, and is also able to identify attackers' attempts to exploit vulnerabilities in the system. Top 10 Threats to Information Security | Georgetown University Modern technology and society's constant connection to the Internet allows more creativity in business than ever before - including the black market. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world. Protecting business data is a growing challenge but awareness is the first step. Here are the top 10 threats to information security today: The Mimetic Virus: Rethinking Mimesis in the Age of Covid ... If we now translate this ancient myth back into the contemporary context of our private caves chained to the continuous flow of daily news, we can take some critical distance and ask: in the case of the Covid-19 pandemic, are we facing a viral/virtual phenomenon in which the media focus makes us lose the sense, not of the reality of the pandemic (people are really dying, and in massive numbers ... The rise of ransomware: How to protect a modern company The rise of ransomware: How to protect a modern company. In 2021, the cost of ransomware attacks is expected to exceed more than $20 billion worldwide. Ransomware has emerged as one of the most ...
Defending Against Modern Malware Attacks in Ruby | by ... Setup with the User Interface Step 1 After navigating to the project list, click on setup under New project. Step 2 Select the "By applying changes manually" section. Step 3 Add configuration details. Now, the user interface will show you several configuration details, such as project_id, shareble_id, and shareable_key.
Home - Coronavirus as a Research Topic for Students ... Coronavirus : A Guide to Understanding the Virus and What Is Known So Far The novel coronavirus that causes COVID-19 is now officially a global pandemic with over 130,000 confirmed cases and over 5,000 deaths. Its path is exponential, and panic is being felt around the globe. But the most important thing you can do to combat the virus is to understand how it works, how it spreads, and to STAY ...
(PDF) Issues regarding cybersecurity in modern world ... it allows to check modern computers in 40-50 minutes, - program can detect and remove up to 200 viruses (most of which can not be detected and removed by other antiviruses), - program works on windows xp, vista, windows 7,8,10, - works in harmony with other antivirus programs, - program can easily be installed on contaminated computers, - term …
The evolution of industrial cybersecurity and contemporary ... With the introduction of IT asset management tools, it is now possible to monitor and manage the devices connected to the network, including the access and security status of each device. Secure wireless access points with appropriate access rights and guest Wi-Fi are now available in all areas where required.
A Dependable Cryptocurrency Wallet Keeps Your Digital ... This is a software application. Its function is to interact with various blockchains. It also serves to save and store your private and public keys. With its aid, you may receive or send cryptos. Your wallet will also help you keep track of your cryptocurrency balance. Features of a Reliable Cryptocurrency Wallet
15 Safest Porn Sites: Best Virus Free Sites ... - LA Weekly The industry standard company Mindgeek provides secure online protection. While the company has had some controversies in the past, they have been related to contested video publishing rights and...
CrowdStrike Guide to Frictionless Zero Trust for Modern ... Observations from the front lines of Incident Response & Proactive Cybersecurity Services in 2019 - and key insights for 2020. Read Report. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from ...
Global security challenges and strategy - Brookings Global security challenges and strategy. Thomas Wright Tuesday, March 2, 2021. Editor's Note: Thomas Wright testified before the Senate Committee on Armed Services during its hearing on "Global ...
Exam 1 BCIS Flashcards - Quizlet With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer. Mobile. Which of the following category of users works on a computer while away from a main office, home office, or school? Facebook.
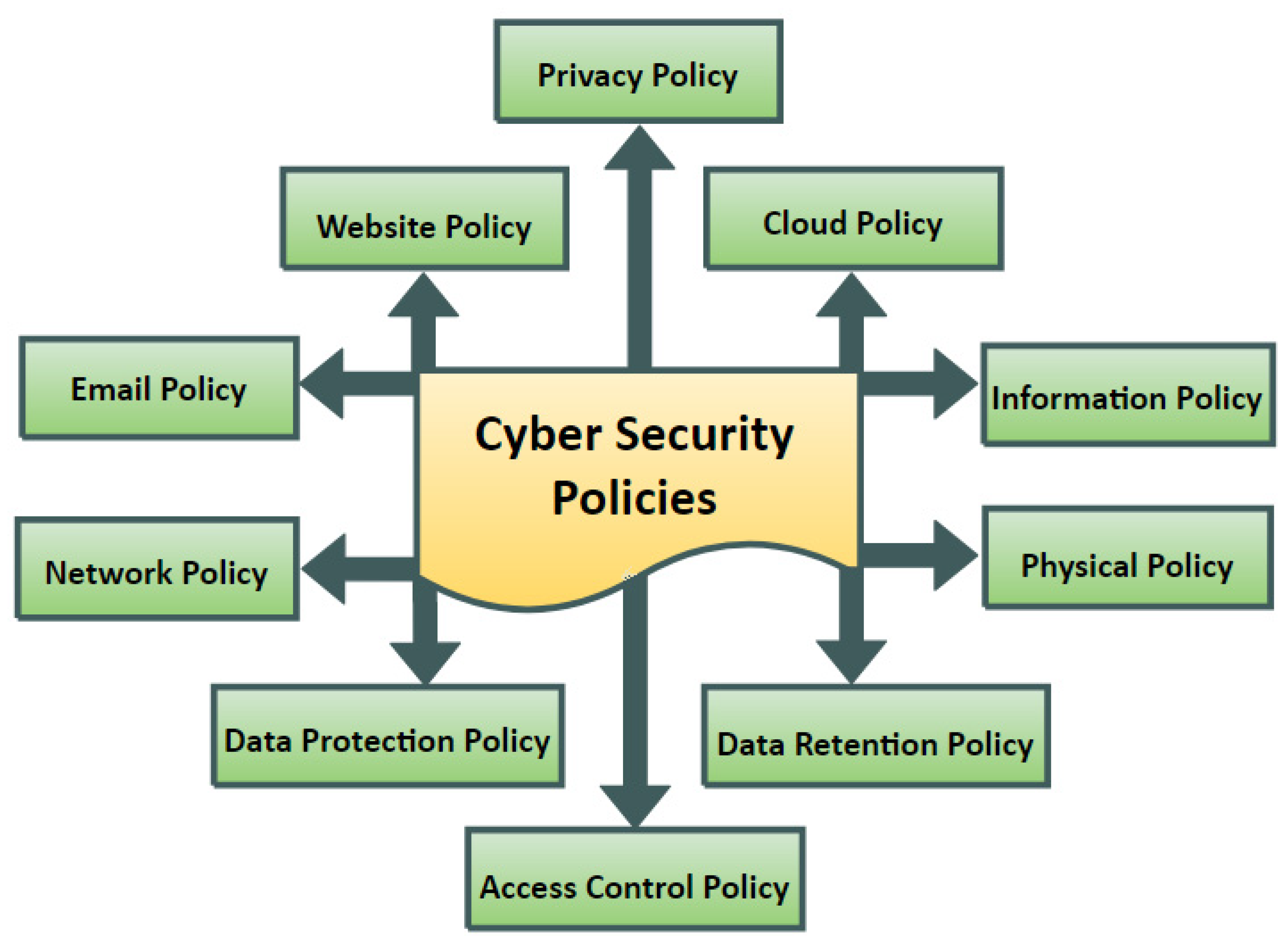
Imperativeness of cybersecurity in the contemporary world As we know that future generation depends on a collective source of IT industry so enabling a secured system get into a big deal. It reduces the risk factors of entire sensitive data over a global cloud service. The gone days are used in simple firewalls and antivirus software but the future is not possible to run with these sources.
What is the future of UK leadership in global health ... The UK is a global health leader. Since the concept of 'health security' first came into parlance with the reconceptualisation of HIV/AIDS as a security threat, 1 the UK has been a leader on global health security. This position was solidified by the broader movement towards the securitisation of non‐traditional security threats post 9/11 (and indeed the anthrax attacks). 2
Antivirus evasion techniques show ease in avoiding ... This test simply demonstrates that it is possible to bypass antivirus engines using this methodology. There are still plenty of other methods that can be utilized to bypass all of them. Packaging Exploits With Penetration-Testing Frameworks My next test utilized the popular Metasploit Community Edition penetration-testing framework.
Car Computer Virus? Modern Hackers Could Control Your Car According to Aryeh Goretsky, a researcher at a technology security company called ESET, you shouldn't be too worried. Goretsky states that creating a virus for a car computer is expensive because vehicle manufacturers have proprietary hardware and software. So, attackers could only target one specific make and model at a time.









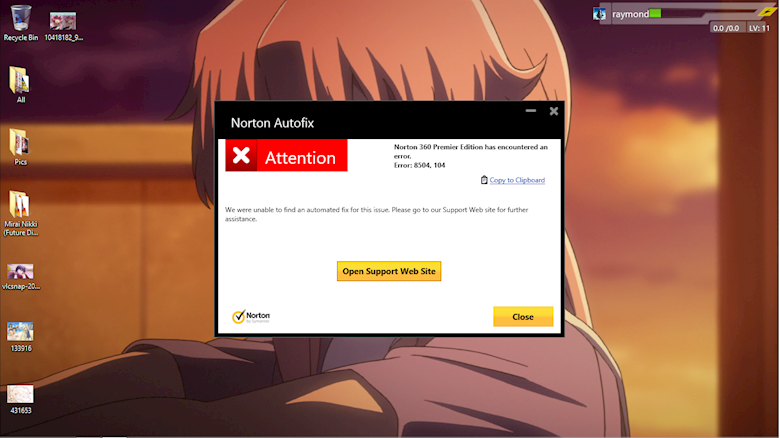


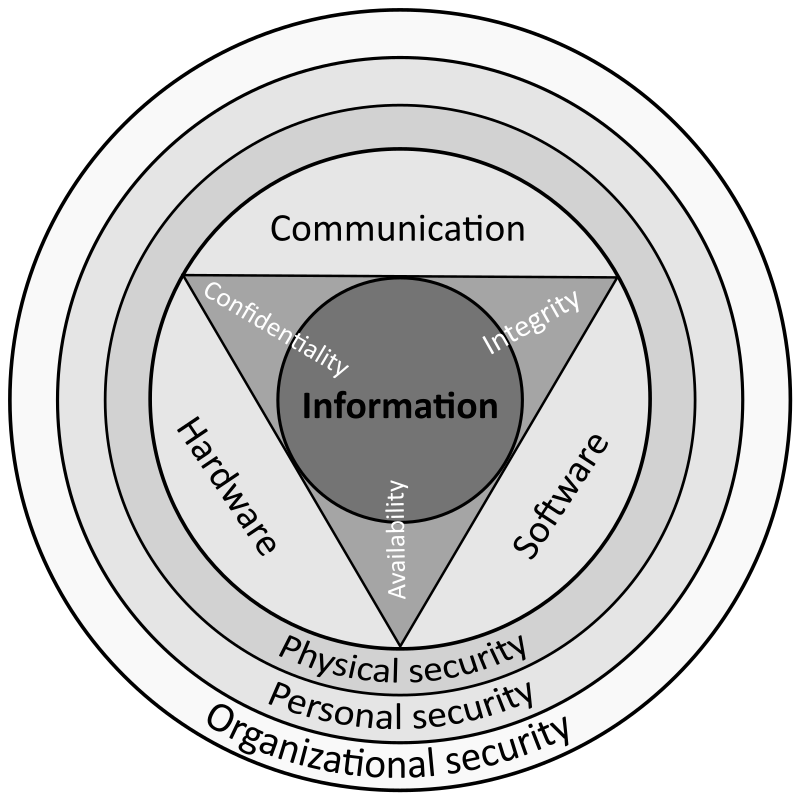






![What to do when antivirus blocks VPN [4 tested solutions]](https://cdn.windowsreport.com/wp-content/uploads/2021/02/vpn.jpg.webp)
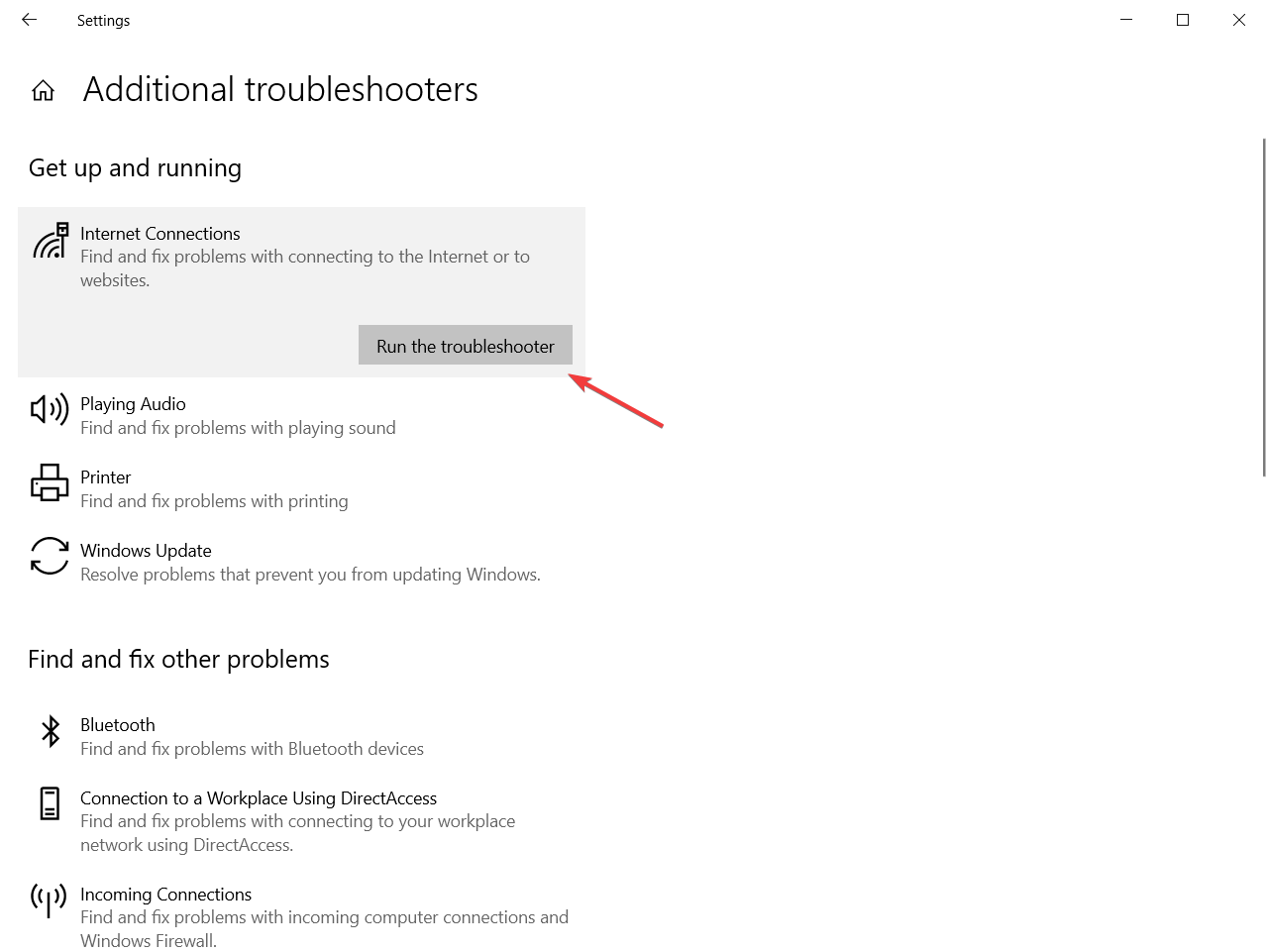







0 Response to "40 with contemporary antivirus protection it is now possible"
Post a Comment